Fri Jan 11 14:23:14 PDT 2019
Rust Server Online Again!
I got tired of playing on other servers (read, not being able to abuse admin privs and also mess with my members) I decided to stop hosting my minecraft server and instead go back to Rust!
I have been watching so many youtube videos of gameplay, I just missed it, and it can be a casual game (especially when your server is brand new and has no other people playing on it.) but farming's boring, so I figured it had to be at least a 2x server. I played on some random 2x server (that spammed you constantly and I hate that) but still had to do too much farming, and also there was no stack changes, so boxes filled up fast. To fix that I have upped my servers limits for most stackable items and went up to 4x. Life is better!
Now you just need to join and have some fun with us! The link above has all the details you could need! Come and play!
Tue Jan 31 17:32:25 PDT 2017
Getting your official raspberry pi camera working on the Synology Surveillance Station v8.0
For reference, I'm using an official raspberry pi camera on a raspberry pi 3 running the motioneyeos found here.
Get your pi up and running on your network, update the UI to allow "expert settings" and make sure to check the option for "Fast Network Camera" is set to "ON".
I also go ahead and disable samba, ftp, motion detection etc as all I really want is the network stream, the synology will be doing the rest of the work. Let it reboot and you should be good to go.
Next is a bit more tricky, on your synology you'll need to have SSH enabled access. Log in and cd over to in my case /volume2/@appstore/SurveillanceStation/device_pack (yours might be on /volume1/.. or /volume3/.. etc.
Create a new file named RaspberryPi.conf and enter in the following text:
[RaspberryPi*Official]
api = rpi1
channel_list = 1
default_channel = 1
resolutions_mjpeg = 640x480, 800x600, 1024x576, 1024x768, 1280x720
fps_mjpeg_[640x480, 800x600, 1024x576, 1024x768, 1280x720] = 1-20
default_image_quality = 5
mjpeg = http
motion = mjpeg
default_username = user
default_password = blankThen stop and start the surveillance station from the synology control panel.
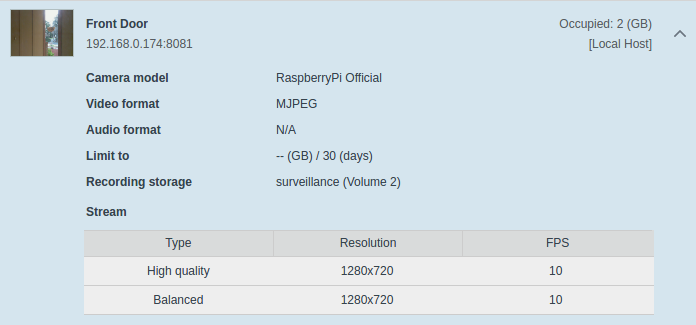
Now when you go back to the surveillance station you will have a camera brand and model for the official raspberry pi camera working!
Set your IP accordingly, set your port to 8081 and your username to "user" and clear out the password, test the connection and enjoy!
Tue Sep 20 13:29:19 PDT 2016
How to setup wifi on your SoC pc be it raspberry pi, orange pi, odroid etc. using wpa_supplicant the RIGHT way!
Why is this the right way? Well quite simply it removes the cleartext of your password from the config file. Also yes I'm aware that it's pretty trivial to deauth and generate alot of traffic and sniff the password right out of the air these days. That still requires local proximity to the network, so there's still an argument to obfuscate your configs as much as possible.
First we are going to list our wireless devices, iwconfig works, but there's actually iw that does the job easier
sudo iw devSee? Isn't that a nice easy to read output?!
Assuming you have a wireless device above, you'll need to scan for your wireless access point's name, odd's are good you already know what it's called and can skip this, but not everyone does so I'm posting this to be complete. Replace wlan0 below with whatever the device's name was above.
sudo iwlist wlan0 scanThis next step will require root though, sudo isn't enough so we'll enter the next 2 commands
sudo su
wpa_passphrase SSID >> /etc/wpa_supplicant.confReplaceing your Access Point's name for the SSID above. Use quotes if there are spaces in the SSID "like so".
This will return you to a blank line. It's waiting for you to type in your Pre Shared Key (PSK) or the password to your wifi, just enter it on this line and press enter.
Now if you check your /etc/wpa_supplicant/wpa_supplicant.conf file you'll see you have your PSK entered and commented out, using a hashed version of it below instead. If your parinoid about computer security like myself, you'll want to delete this line and just leave the hashed version. It should work just fine.
Now you should be good to cycle your wireless card and get connected! Easy enough, just enter the following and you should be up and running! (or just reboot)
sudo ifdown wlan0
sudo ifup wlan0Give it a few seconds to connect and check you should see you all connected
pi@demo:~ $ iw dev
phy#0
Interface wlan0
ifindex 3
wdev 0x1
addr 7c:dd:90:8d:e1:38
ssid Flaming Unicorns
type managed
Sat Sep 3 01:14:40 PDT 2016
Just a sample of some blog stuff
Really this is just a test to figure out some formatting items, and to play with highlight.js to make sure it works, as well as to make it fit my theme just a little bit better.
Another paragraph with not really alot of content, but I guess I should try one of my all too common long run on sentences that are overly detailed for no real reason other then I am really trying to describe my point of view with as little discrepencies or mis-understanding as possible.
Here's a very simple shell script to run on an AWS machine image (AMI) that has the splunk monitoring agent installed, prior to creating an image of it
#!/bin/bash
### Remove Sumo for Splunk Prep
USERNAME='root'
ME=`whoami`
as_user() {
if [ $ME == $USERNAME ] ; then
bash -c "$1"
else
su - $USERNAME -c "$1"
fi
}
as_user "/opt/splunkforwarder/bin/splunk stop && /opt/splunkforwarder/bin/splunk clone-prep-clear-config"
exit 0And a closing line just for tesing 'n stuff.